Last week we reported on a very serious and soon-to-be a very exploitable vulnerability that probably impacts you and your organization. This vulnerability goes by the name of SIGRed.
Now that the dust has settled and we have all diligently patched our servers, set up monitoring and assured our execs that we are all clear, we can take a step back and ask some more involved questions about what this actually means, and where systems or procedures may have fallen short in response to this announcement.
Litmus Test
This definitely is not the first high severity vulnerability out there and will not be the last. Having a plan in place – whether that is an emergency patching procedure, having thoughtful system auditing, knowing the software the powers your business, or even checking out what is trending on Twitter is more than a good start.
Next time you are around the virtual coffee machine you should take the time to ask your risk team, your execs or your friendly IT team some choice questions to understand the response process for these front-page articles.
Remember the old saying: It takes a village to raise a child and it takes organization wide buy in to produce an effective IT Security strategy.
Key questions
- Do you know about the SIGRed vulnerability?
- Do you know if we are vulnerable?
- Have we patched or mitigated this vulnerability?
- Does the business have a out-of-band patch window?
- Do we even have patch Windows?
- How do we as an organization receive intelligence on these incidents?
- How do we monitor for signs these vulnerabilities are being exploited in our network?
- What is the ideal time to remediate these issues?
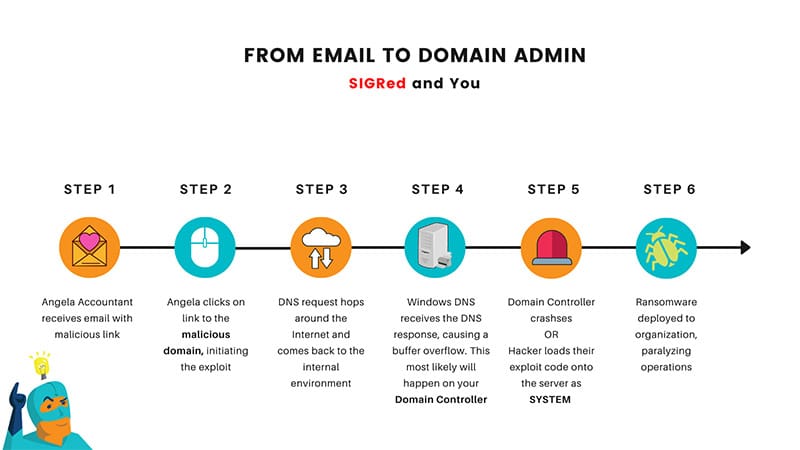
From Email to Domain Admin
Jinba Man has been busy at work mapping out what the future will probably look like once an exploit for this vulnerability is publicly available.
End of life?
Windows Server 2008 was put out to pasture (end of life) in January 2020, meaning Microsoft will no longer support this platform through software update services unless you work for a company that has very deep pockets to receive extended support.
Browsing through the Microsoft patch catalogue a very keen eye will see this patch has been released to the public for Windows Server 2008. Reading between the lines here we can assert that Microsoft has done the risk assessment for this vulnerability and have high confidence in knowning this will lead to common exploits in the future and so they have given out a freebie.
If you are still running Windows Server 2008 it is time to migrate away.
Where to from here?
At a minimum apply the workaround suggested in the original post. Go the extra mile (and you should) to patch and reboot your vulnerable systems.
While you are waiting for the server to reboot, take a moment to reflect on the questions above. These are all important elements that make up a secure environment to let your people work their best, without interruption.
Don’t know where to start?
We do. 👇
Failed the litmus test? Don’t know where to start?
Begin discovery and reach out to Jinba
